1.4 创建用户并更改ssh默认端口
创建用户
创建用户的命令很简单:
adduser username
下面演示创建一个名为scott的用户,并将其添加到sudo group中
adduser scott
usermod -aG sudo scott
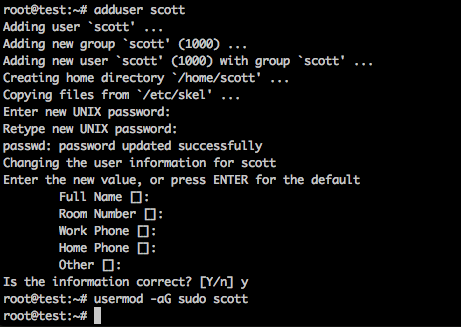
这时,你cd到/home目录,执行ls就可以看到所有非系统用户目录(root为/root)

更改ssh默认端口
ssh默认端口是22,这就意味着这个端口对所有人都是透明的,假如你买了台服务器,我就能猜到你的端口是22,首先猜到了你的用户名root,虽然不知道你的密码,但是也又被破解的风险!
所以有必要改下ssh端口,端口的改动伴随着防火墙的改动(当然你也可以不改,所以大门都开启). 任何关于防火墙的操作都有可能导致下次ssh无法登录, 所以修改完配置之后不要立即退出,cmd + T 新开一个终端窗口再试.
更改默认端口,提高安全等级
端口范围 0-65536,但0-1024建议不要使用(一般会被系统占用)
先登录vps
sudo vi /etc/ssh/sshd_config
cmd+t再开一个端口,记录登录的状态,如果是你修改出了问题或者忘了端口,可能导致你下次连登录都登不进去了
# 这句话干了2件事,首先关掉了默认的22端口,其次你必须在39999登录才登的进去
Port 39999
# 找到 useDNS 保证它是no, 在最末尾增加一行UseDNS no
UseDNS no
# 允许server_manager scott从39999端口登录
AllowUsers server_manager scott
保存,退出, 开39999端口,重启ssh
# ubuntu:
sudo service ssh restart
# centos:
systemctl restart sshd.service 或 service sshd restart
新开一个窗口
ssh -p 39999 server_manager@ipv4
# 注意密码是创建用户的密码, 改密码用 passwd username 如果登陆成功,恭喜端口改掉了
下面是ubuntu14的一些配置
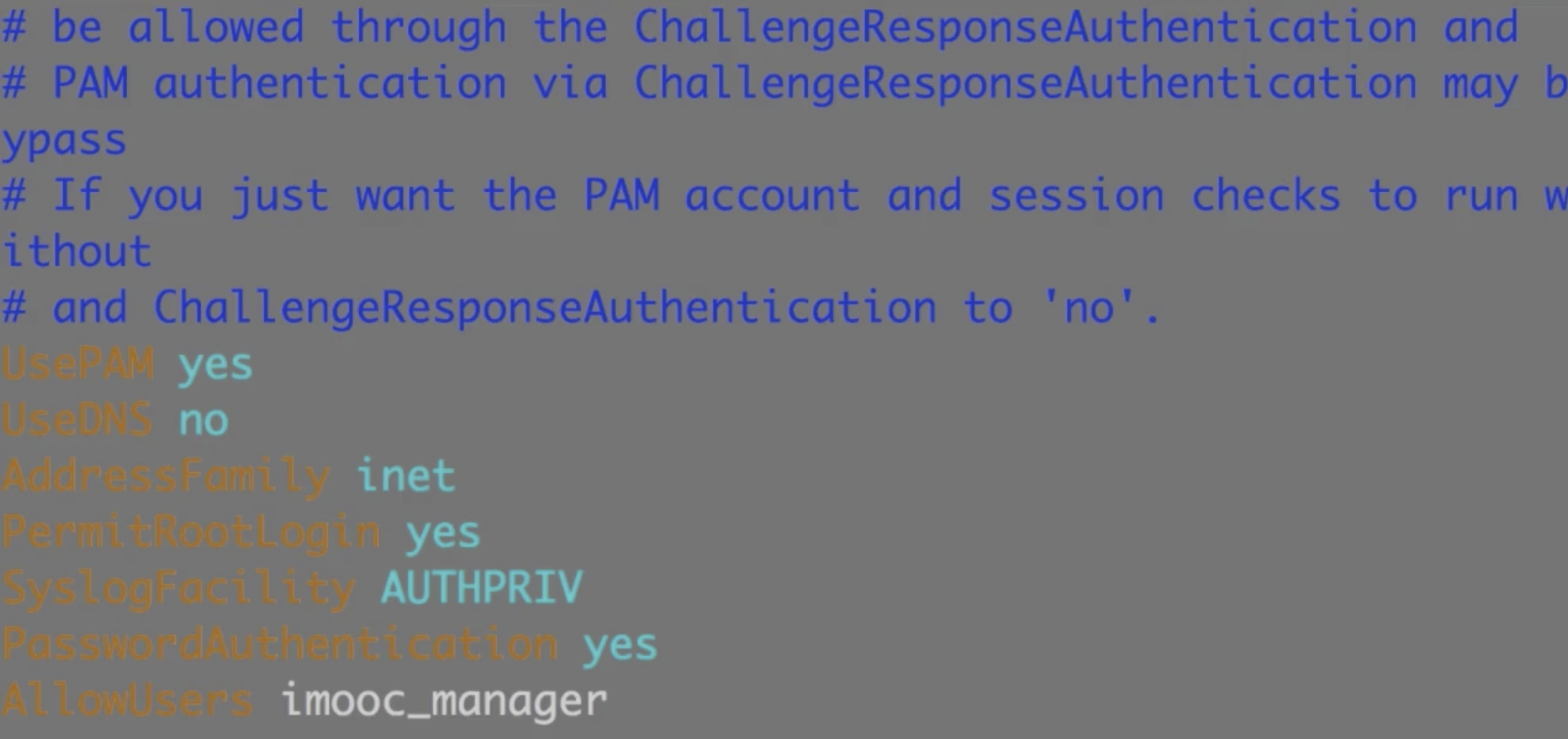
下面是ubuntu16的默认配置
# Package generated configuration file
# See the sshd_config(5) manpage for details
# What ports, IPs and protocols we listen for
Port 22
# Use these options to restrict which interfaces/protocols sshd will bind to
#ListenAddress ::
#ListenAddress 0.0.0.0
Protocol 2
# HostKeys for protocol version 2
HostKey /etc/ssh/ssh_host_rsa_key
HostKey /etc/ssh/ssh_host_dsa_key
HostKey /etc/ssh/ssh_host_ecdsa_key
HostKey /etc/ssh/ssh_host_ed25519_key
#Privilege Separation is turned on for security
UsePrivilegeSeparation yes
# Lifetime and size of ephemeral version 1 server key
KeyRegenerationInterval 3600
ServerKeyBits 1024
# Logging
SyslogFacility AUTH
LogLevel INFO
# Authentication:
LoginGraceTime 120
PermitRootLogin yes
StrictModes yes
RSAAuthentication yes
PubkeyAuthentication yes
#AuthorizedKeysFile %h/.ssh/authorized_keys
# Don't read the user's ~/.rhosts and ~/.shosts files
IgnoreRhosts yes
# For this to work you will also need host keys in /etc/ssh_known_hosts
RhostsRSAAuthentication no
# similar for protocol version 2
HostbasedAuthentication no
# Uncomment if you don't trust ~/.ssh/known_hosts for RhostsRSAAuthentication
#IgnoreUserKnownHosts yes
# To enable empty passwords, change to yes (NOT RECOMMENDED)
PermitEmptyPasswords no
# Change to yes to enable challenge-response passwords (beware issues with
# some PAM modules and threads)
ChallengeResponseAuthentication no
# Change to no to disable tunnelled clear text passwords
#PasswordAuthentication yes
# Kerberos options
#KerberosAuthentication no
#KerberosGetAFSToken no
#KerberosOrLocalPasswd yes
#KerberosTicketCleanup yes
# GSSAPI options
#GSSAPIAuthentication no
#GSSAPICleanupCredentials yes
X11Forwarding yes
X11DisplayOffset 10
PrintMotd no
PrintLastLog yes
TCPKeepAlive yes
#UseLogin no
#MaxStartups 10:30:60
#Banner /etc/issue.net
# Allow client to pass locale environment variables
AcceptEnv LANG LC_*
Subsystem sftp /usr/lib/openssh/sftp-server
# Set this to 'yes' to enable PAM authentication, account processing,
# and session processing. If this is enabled, PAM authentication will
# be allowed through the ChallengeResponseAuthentication and
# PasswordAuthentication. Depending on your PAM configuration,
# PAM authentication via ChallengeResponseAuthentication may bypass
# the setting of "PermitRootLogin without-password".
# If you just want the PAM account and session checks to run without
# PAM authentication, then enable this but set PasswordAuthentication
# and ChallengeResponseAuthentication to 'no'.
UsePAM yes